2.1 Networking

Introduction
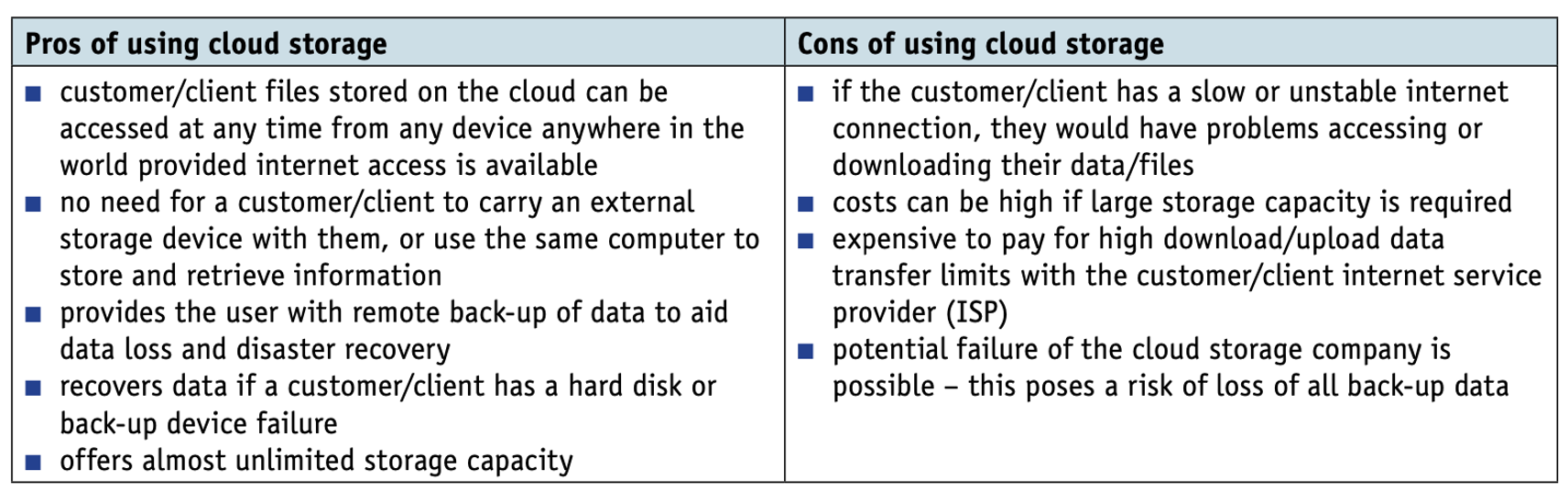
One of the earliest forms of networking, circa 1970 in the USA, was the Advanced Research Projects Agency Network (ARPAnet).
This was an early form of packet switching wide area network (WAN) connecting a number of large computers in the Department of Defense.
It later expanded to include university computers. It is generally agreed that ARPAnet developed the technical platform for what we now call the internet.
A network can be anything from a connection of two computers to millions of computers that are connected together worldwide using the Internet.
Networks are classified based on the nature of the connection as LAN, WAN, PAN, MAN, SAN, WPAN, VPN.
Advantages and disadvantages of using networks
| Advantages | Disadvantages |
|---|---|
| Shared devices | Cost for cables |
| Cheaper software licenses | Management complex |
| Share files | Break down |
| Back up files | Malware and hacking |
| User communication | |
| Network oversee |
Networks
What are the advantages of the network?
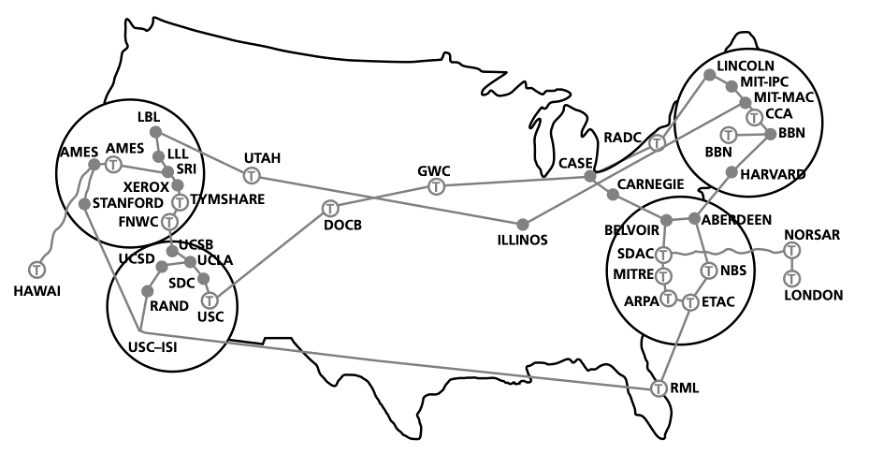
Local Area Network (LAN)
LANs are usually contained within one building, or within a small geographical area.
A typical LAN consists of a number of computers and devices (such as printers) connected to hubs or switches.
One of the hubs or switches is usually connected to a router and/or modem to allow the LAN to connect to the internet or become part of a wide area network (WAN).
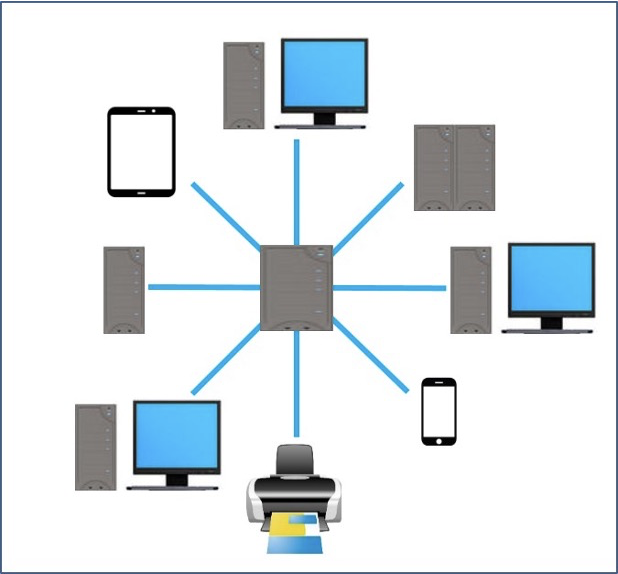
Wide area networks (WANs)
Wide area networks (WANs) are used when computers or networks are situated a long distance from each other (for example, they may be in different cities or on different continents).
If a number of LANs are joined together using a router or modem, they can form a WAN.
WAN = LAN + LAN + …… + LAN
Networks
Which is usually contained within one building, or within a small geographical area.
Wireless LANs (WLANs)
Wireless LANs (WLANs) are similar to LANs but there are no wires or cables. In other words, they provide wireless network communications over fairly short distances using radio or infrared signals instead of using cables.
Devices, known as wireless access points (WAPs), are connected into the wired network at fixed locations.
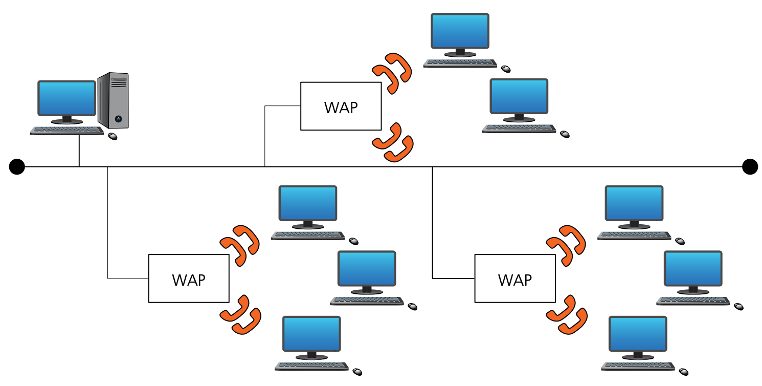
Networks
Devices, known as( ), are connected into the wired network at fixed locations.
Client-server model
- The client-server model uses separate dedicated servers and specific client workstations; client computers will be connected to the server computer(s).
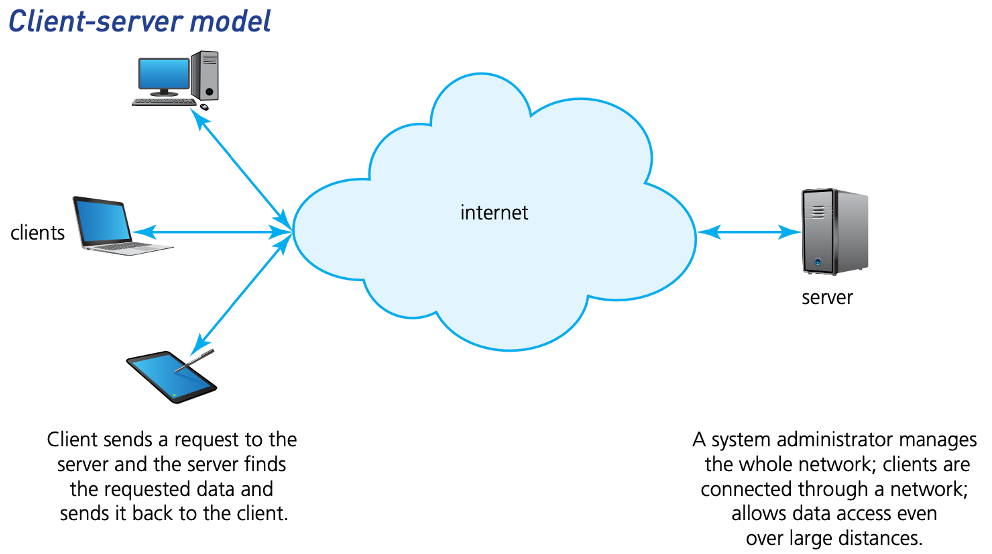
- A company/user would choose a client-server network model for the following reasons:
- The company/user has a large user-base.
- Access to network resources needs to be properly controlled.
- There is a need for good network security.
- The company requires its data to be free from accidental loss.
Peer-to-peer model
- The peer-to-peer model does not have a central server. Each of the nodes (workstations) on the network can share its files with all the other nodes, and each of the nodes will have its own data.
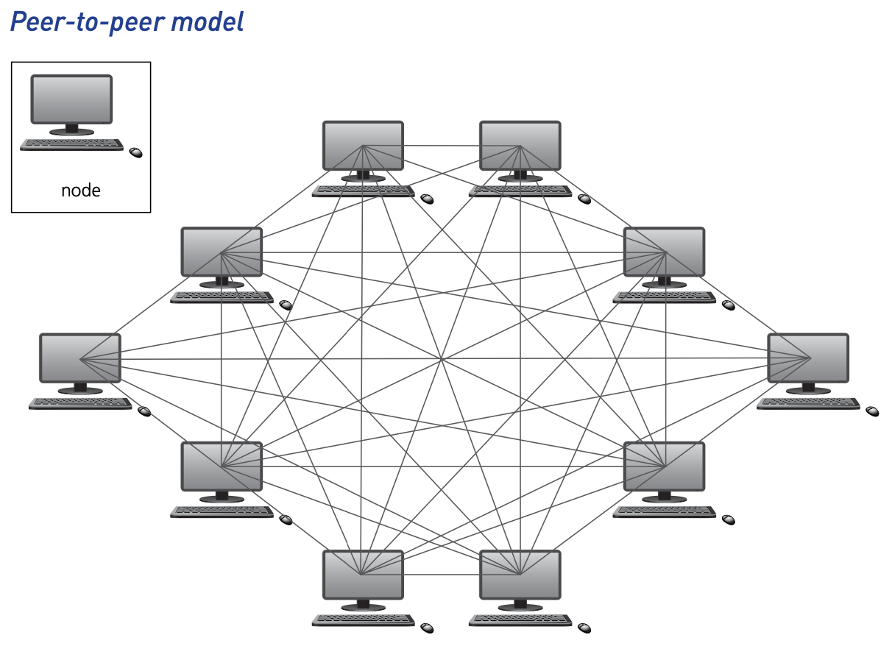
A user would choose the peer-to-peer network model for one or more of following reasons:
- The network of users is fairly small.
- There is no need for robust security.
- They require workstation-based applications rather than being server-based.
Networks
If we want to control network resources, which model should we choose?
Thin clients and thick clients
- The client-server model offers thin clients and thick clients. These can often refer to both hardware and software.
Thin client
- A thin client is heavily dependent on having access to a server to allow constant access to files and to allow applications to run uninterrupted.
Thick client
- A thick client can either be a device or software that can work offline or online; it is still able to do some processing whether it is connected to a server or not.
comparison for hardware
| Pros | Cons | |
|---|---|---|
| Thick client | - more robust - clients have more control | - less secure - update data software individually - data integrity issues |
| Thin client | - less expensive to expand - all devices are linked to a server - server can offer protection against hacking and malware | - high reliance on the server - high start-up costs |
comparison for software
| Thin client | Thick client |
|---|---|
| - always relies on a connection to a remote server or computer for it to work | - can run some of the features of the software even when not connected to a server |
| - requires very few local resources (such as SSD, RAM memory or computer processing time) | - relies heavily on local resources |
| - relies on a good, stable and fast network connection for it to work | - more tolerant of a slow network connection |
| - data is stored on a remote server or computer | - can store data on local resources such as HDD or SSD |
Networks
A ( ) is heavily dependent on having access to a server to allow constant access to files and to allow applications to run uninterrupted.
Network topologies
- There are many ways to connect computers to make complex networks. Here we will consider:
bus networks
star networks
mesh networks
hybrid networks
Networks
What network topologies are currently in use?
Bus networks
- A bus network topology uses a single central cable to which all computers and devices are connected. It is easy to expand and requires little cabling. Data can only travel in one direction; if data is being sent between devices then other devices cannot transmit.

Star networks
- A star network topology uses a central hub/switch and each computer/device is connected to the hub/switch. Data going from host to host is directed through the central hub/switch.
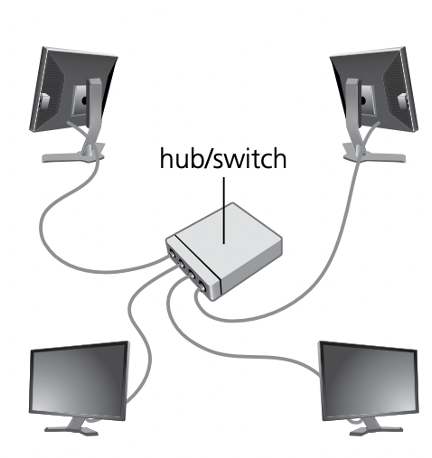
Mesh networks
There are two types of mesh network topologies: routing and flooding.
Routing works by giving the nodes routing logic so that data is directed to its destination by the shortest route and can be re-routed if one of the nodes in the route has failed.
Flooding simply sends the data via all the nodes and uses no routing logic, which can lead to unnecessary loading on the network.
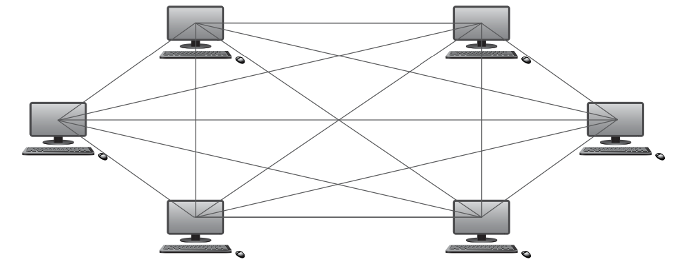
Hybrid networks
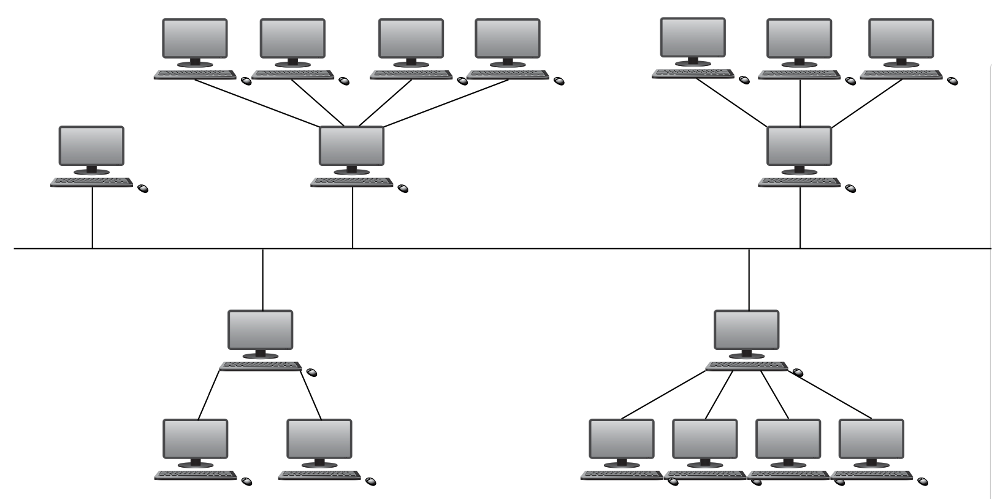
- A hybrid network is a mixture of two or more different topologies (bus and star, bus and mesh, and so on).
Networks
A ( ) topology uses a single central cable to which all computers and devices are connected.
Networks
A ( ) topology uses a central hub/switch and each computer/device is connected to the hub/switch.
Networks
Which network topology is in the following picture?
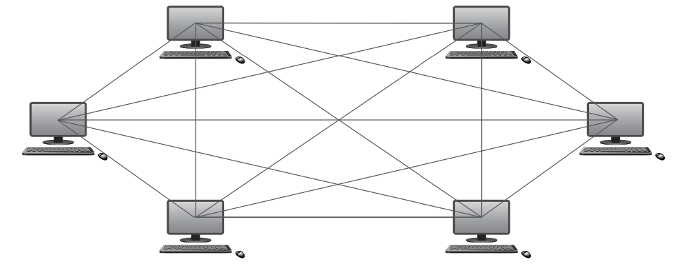
Networks
A ( ) is a mixture of two or more different topologies.
Public and private cloud computing
There are three common systems, public cloud, private cloud and hybrid cloud:
Public cloud is a storage environment where the customer/client and cloud storage provider are different companies.
Private cloud is storage provided by a dedicated environment behind a company firewall. Customer/client and cloud storage provider are integrated and operate as a single entity.
Hybrid cloud is a combination of private and public clouds. Some data resides in the private cloud and less sensitive/less commercial data can be accessed from a public cloud storage provider.
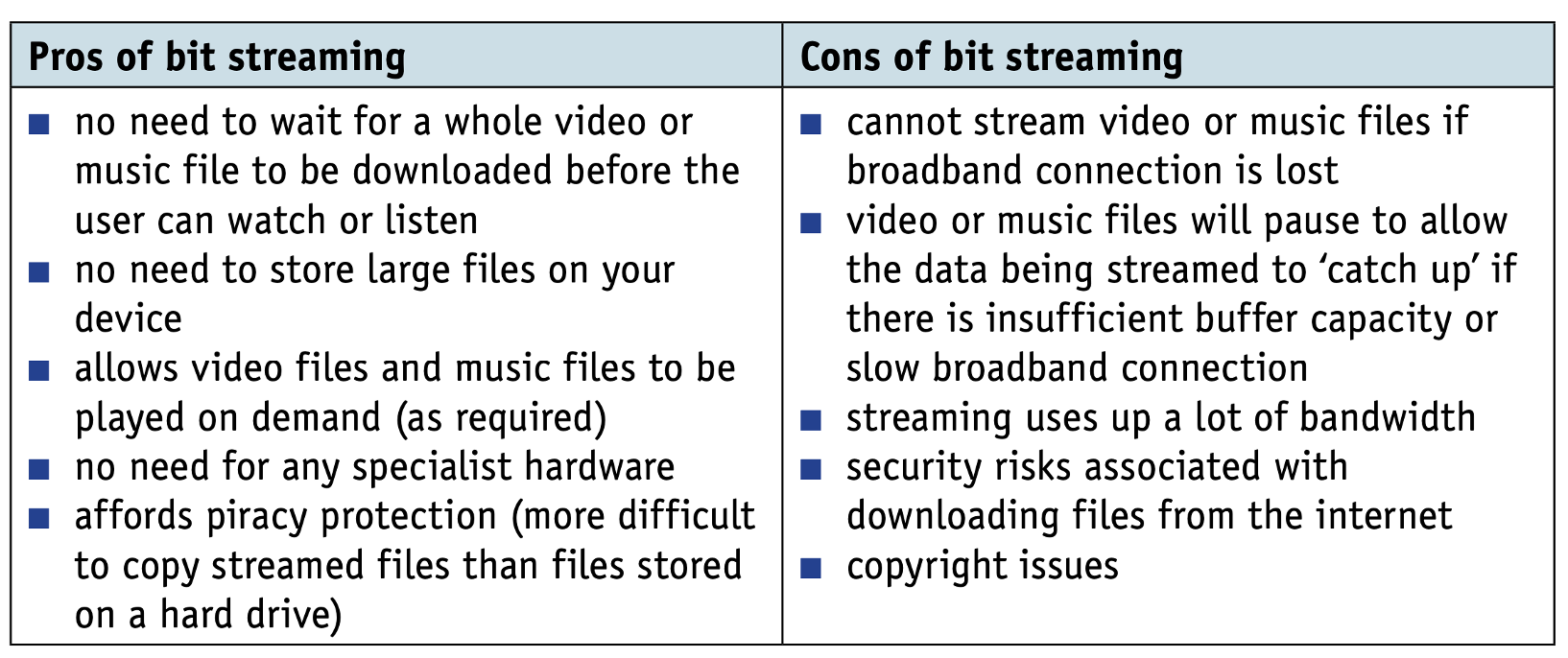
Pros and cons of using cloud storage
Networks
( ) is a storage environment where the customer/client and cloud storage provider are different companies.
Wired and wireless networking
Wireless
Both Wi-Fi and Bluetooth offer wireless communication between devices. They both use electromagnetic radiation as the carrier of data transmission.
When a device wants to communicate, it picks one of the 79 channels at random. If the channel is already being used, it randomly picks another channel. This is known as spread spectrum frequency hopping. Bluetooth creates a secure wireless personal area network (WPAN) based on key encryption.
Wireless connectivity uses electromagnetic radiation: radio waves, microwaves or infrared.

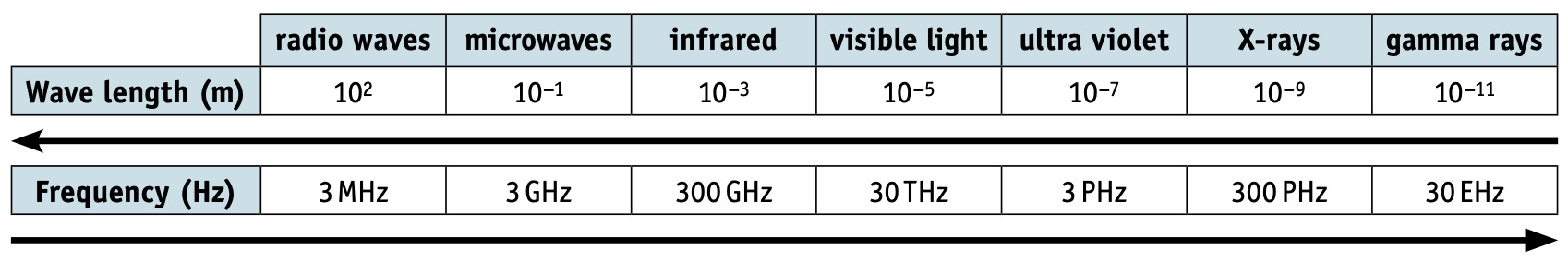
Use of satellites
- The use of microwaves and radio waves was previously mentioned as a method for allowing Wi-Fi connectivity in networks.
- These methods are perfectly satisfactory for short distances, the electromagnetic waves carry the signals, but the curvature of the Earth prevents such methods transmitting data globally.
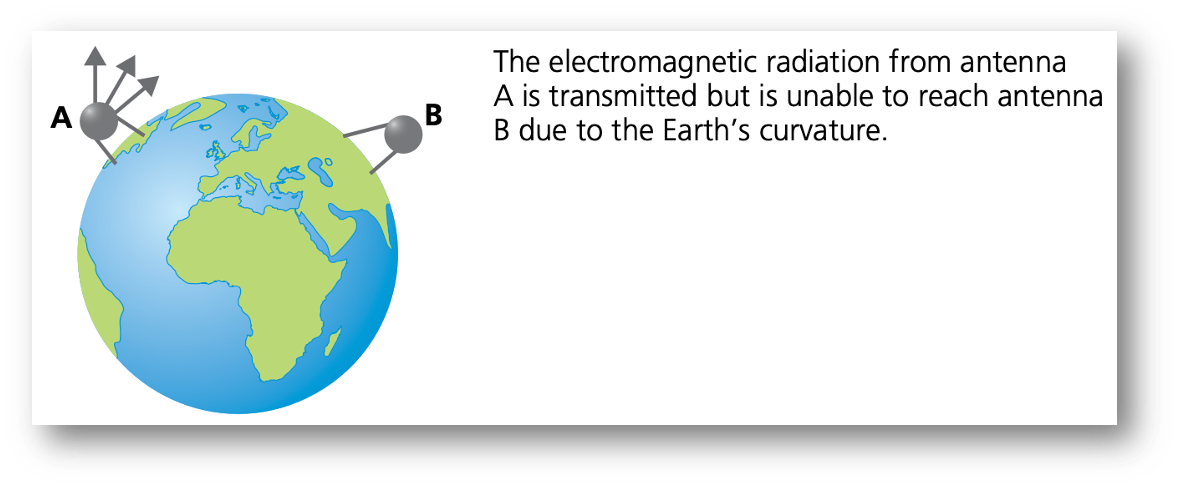
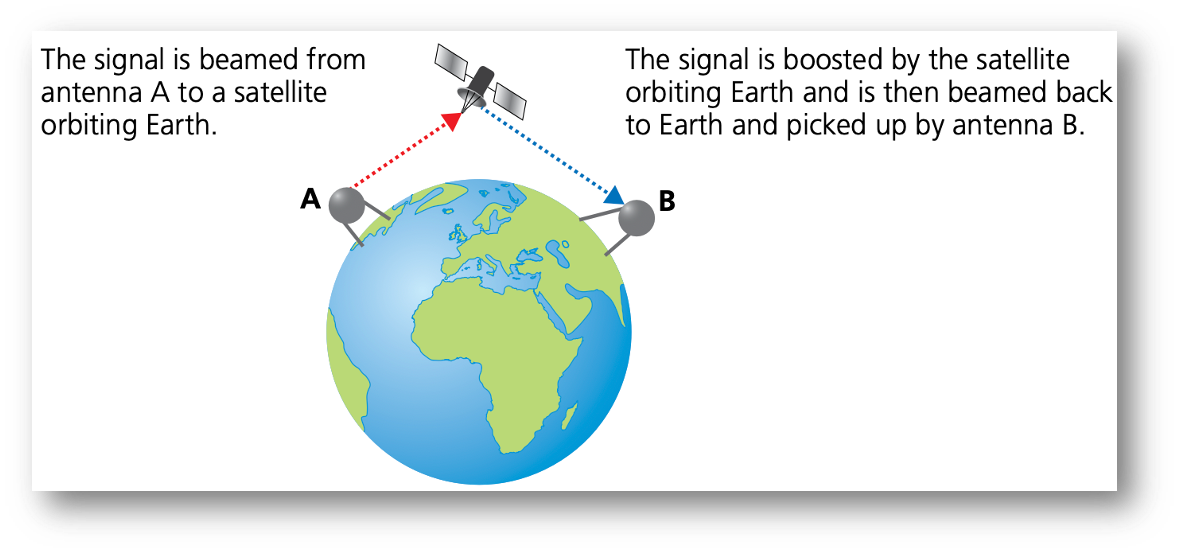
Networks
Both and offer wireless communication between devices. They both use electromagnetic radiation as the carrier of data transmission.
Wired
There are three main types of cable used in wired networks:
- Twisted pair cable
- coaxial cable
- fibre optic cable
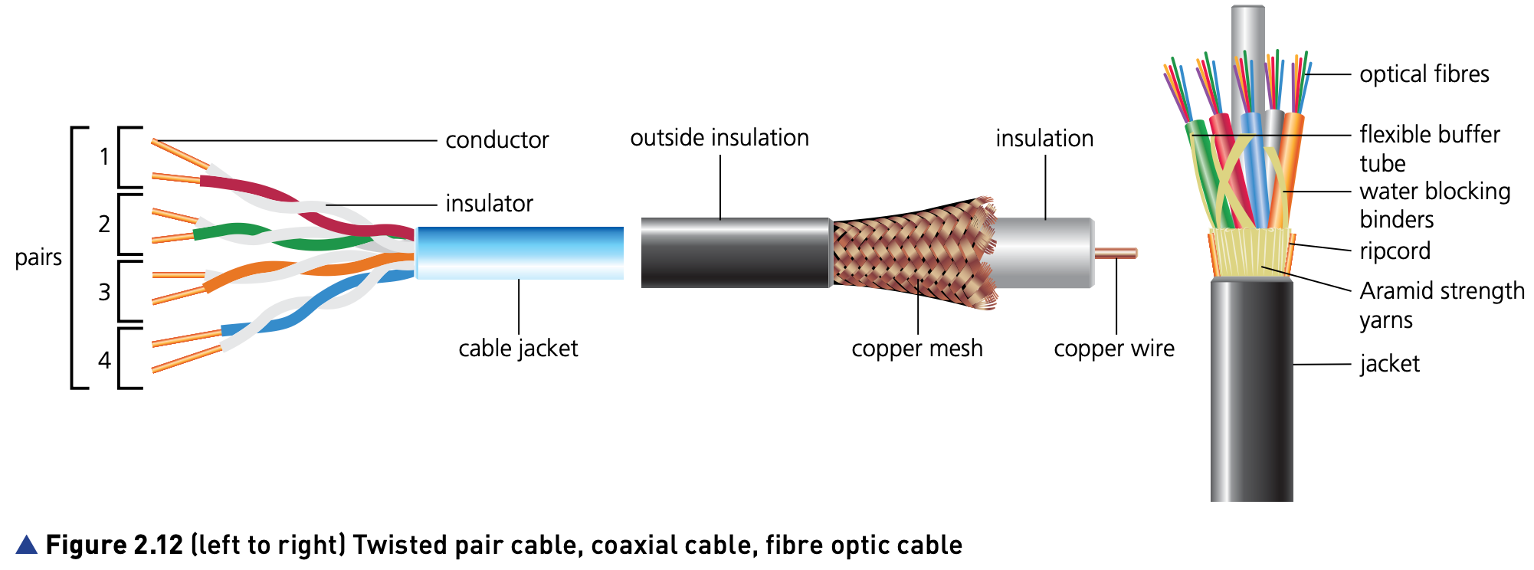
Twisted pair cables are the most common cable type used in LANs. However, of the three types of cable, it has the lowest data transfer rate and suffers the most from external interference.
Coaxial cables are the most commonly used cables in MANs and by cable television companies. The cost of coaxial cables is higher than twisted pair cables but they offer a better data transfer rate and are affected less by external interference.
Fibre optic cables are most commonly used to send data over long distances, because they offer the best data transfer rate, the smallest signal attenuation and have a very high resistance to external interference.
Wired vs wireless
| Wireless | Wired | |
|---|---|---|
| Reliability | More interference | Reliable |
| Speed | Lower | Faster |
| Cost | Expensive | Cheaper |
| Danger | Less data security | Tripping hazard |
Networks
The cost of is higher than twisted pair cables but they offer a better data transfer rate and are affected less by external interference.
Hub
- Hubs are hardware devices that can have a number of devices or computers connected to them.
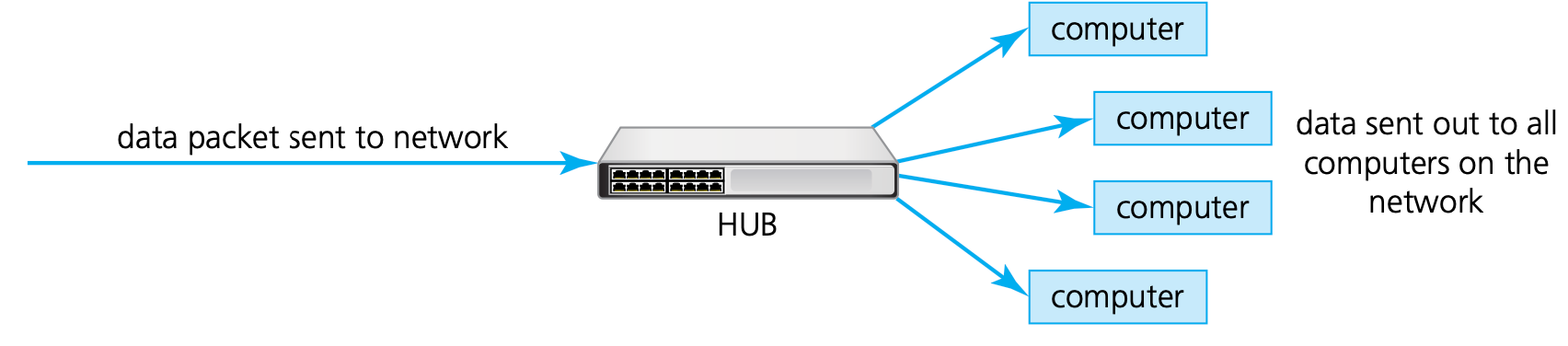
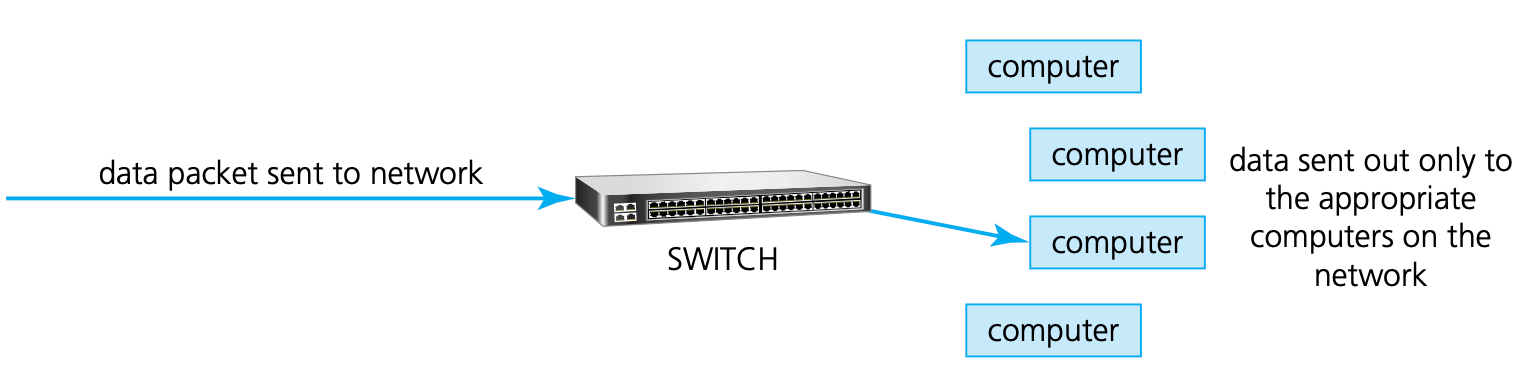
Switch
- Switches are similar to hubs, but are more efficient in the way they distribute the data packet. As with hubs, they connect a number of devices or computers together to form a LAN.
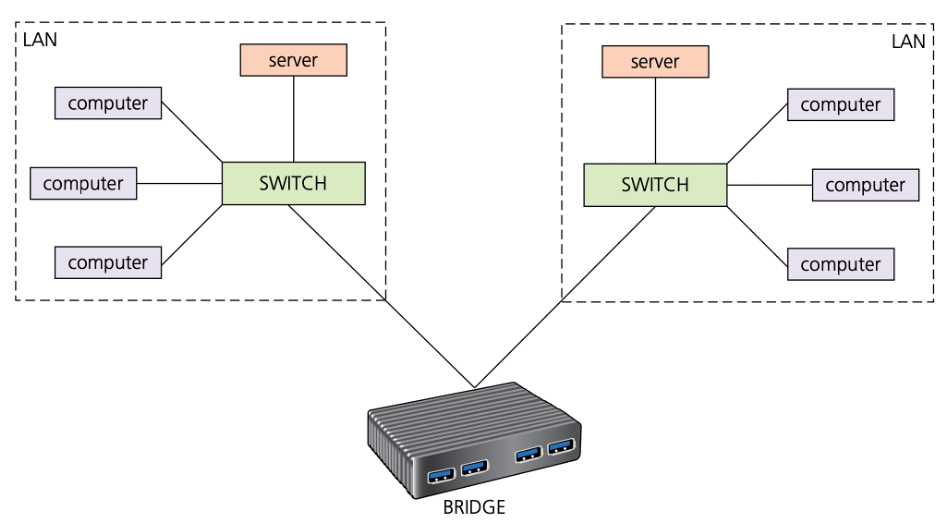
Bridges
- Bridges are devices that connect one LAN to another LAN that uses the same protocol (communication rules). They are often used to connect together different parts of a LAN so that they can function as a single LAN.
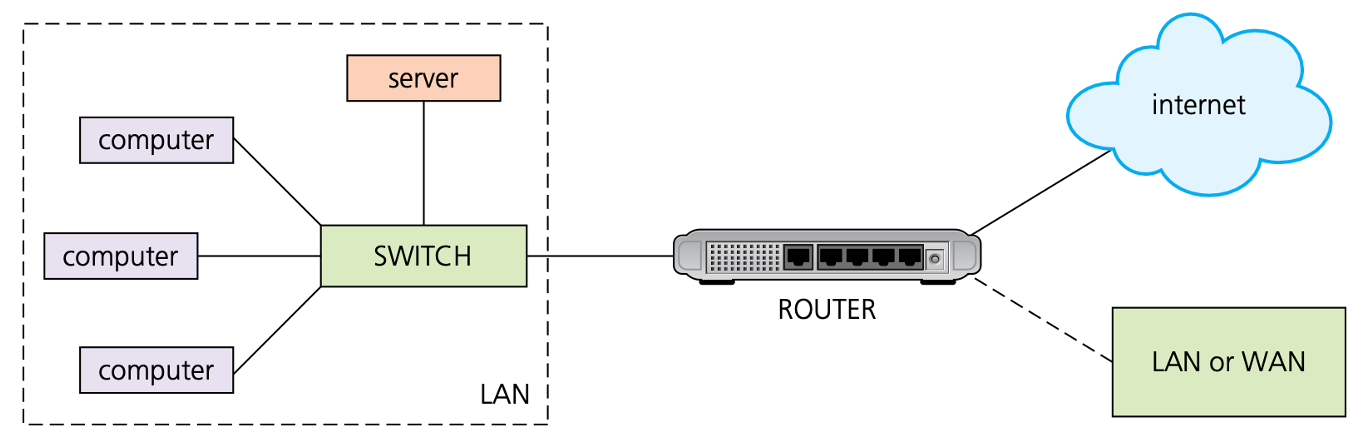
Routers
- Routers enable data packets to be routed between the different networks for example, to join a LAN to a WAN. The router takes data transmitted in one format from a network and converts the data to a protocol and format understood by another network, thereby allowing them to communicate via the router.
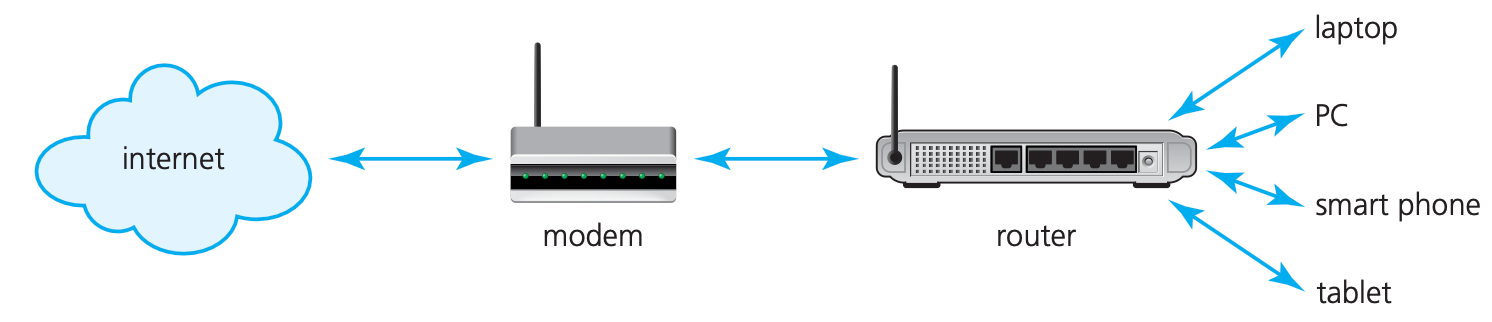
Modem
- Modern computers work with digital data, whereas many of the public communication channels still only allow analogue data transmission. To allow the transmission of digital data over analogue communication channels we need to use a modem (modulator demodulator).
Repeater
- When signals are sent over long distances, they suffer attenuation or signal loss. Repeaters are devices which are added to transmission systems to boost the signal so it can travel greater distances.
Gateway
- A gateway is a network point (or node) that acts as an entrance to another network. Gateways can also act as routers, firewalls or servers – in other words, any device that allows traffic to flow in and out of the networks. Gateways can be wired or wireless devices.
Network interface card (NIC)
- A network interface card (NIC) is needed to allow a device to connect to a network (such as the internet). It is usually part of the device hardware and frequently contains the MAC address generated at the manufacturing stage.
Wireless network interface card/controller (WNIC)
Wireless network interface cards/controllers (WNICs) are the same as the more ordinary NICs, in that they are used to connect devices to the internet or other networks. They use an antenna to communicate with networks via microwaves and normally simply plug into a USB port or can be internal integrated circuit plug in.

Ethernet
Ethernet is a protocol used by many wired LANs. It was adopted as a standard by the Institute of Electrical and Electronic Engineers (IEEE) and Ethernet is also known as IEEE 802.3.
A network using Ethernet is made up of:
- a node (any device on the LAN)
- medium (path used by the LAN devices, such as an Ethernet cable)
- frame (data is transmitted in frames which are made up of source address and destination address – the addresses are often the MAC address).
Networks
( ) are hardware devices that can have a number of devices or computers connected to them.
Networks
( ) are devices which are added to transmission systems to boost the signal so it can travel greater distances.
Networks
( ) are devices that connect one LAN to another LAN that uses the same protocol (communication rules). They are often used to connect together different parts of a LAN so that they can function as a single LAN.
Networks
To allow the transmission of digital data over analogue communication channels we need to use a ( ).
Networks
A ( ) is a network point (or node) that acts as an entrance to another network.
Networks
( ) enable data packets to be routed between the different networks for example, to join a LAN to a WAN.
Networks
A ( ) is needed to allow a device to connect to a network (such as the internet).
Networks
( ) are similar to hubs, but are more efficient in the way they distribute the data packet. As with hubs, they connect a number of devices or computers together to form a LAN.
Networks
is a protocol used by many wired LANs. It was adopted as a standard by the Institute of Electrical and Electronic Engineers (IEEE) and Ethernet is also known as IEEE 802.3.
Carrier sense multiple access with collision detection (CSMA/CD)
Conflicts
- When using Ethernet, it is possible for IP addresses to conflict. This may occur if devices on the same network have been given the same IP address; without a unique IP address it is not possible to connect to a network.
Collisions
Ethernet supports broadcast transmission and are used to send messages to all devices connected to a LAN. The risk is that two messages using the same data channel could be sent at the same time, leading to a collision. Carrier sense multiple access with collision detection (CSMA/CD) was developed to try and resolve this issue.
Collison detection depends on simple physics: when a frame is sent it causes a voltage change on the Ethernet cable.
When a collision is detected, a node stops transmitting a frame and transmits a ‘jam’ signal and then waits for a random time interval before trying to resend the frame.
CSMA/CD protocol will define the random time period for a device to wait before trying again.
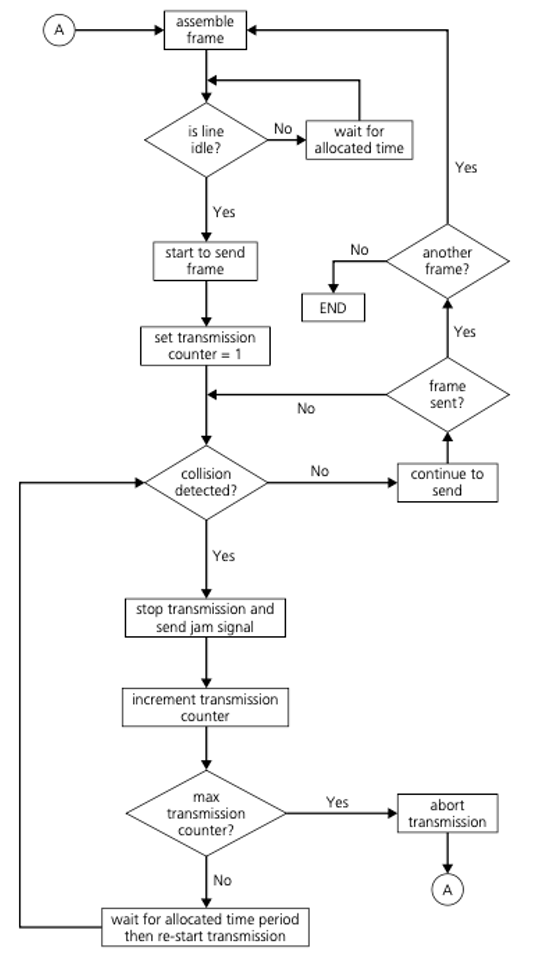
Networks
Ethernet supports broadcast transmission and are used to send messages to all devices connected to a LAN. The risk is that two messages using the same data channel could be sent at the same time, leading to a collision. (CSMA/CD) was developed to try and resolve this issue.
Bit streaming
- Bit streaming is a contiguous sequence of digital bits sent over the internet or a network that requires a high speed data communication link (such as fast broadband).
- Since bit streaming often involves very large files (such as video) it is necessary for the files to undergo some data compression before transmission.
- It is also necessary to have some form of buffering to ensure smooth playback of the media files.
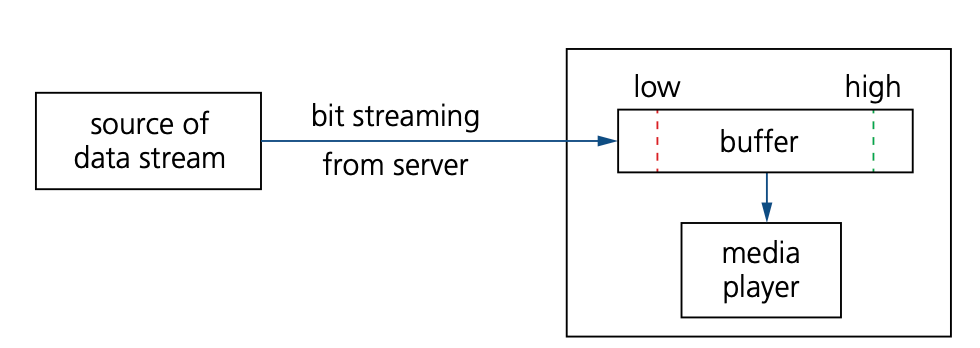
- Bit streaming can be either on demand or real time.
On demand
- Digital files stored on a server are converted to a bit streaming format (encoding takes place and the encoded files are uploaded to a server).
- A link to the encoded video/music file is placed on the web server to be downloaded.
- The user clicks on the link and the video/music file is downloaded in a contiguous bit stream.
- Because it is on demand, the streamed video/music is broadcast to the user as and when required.
- It is possible to pause, rewind and fast forward the video/music if required.
Real time
- An event is captured by camera and microphone and is sent to a computer. The video signal is converted (encoded) to a streaming media file.
- The encoded file is uploaded from the computer to the dedicated video streaming server.
- The server sends the encoded live video to the user’s device.
- Since the video footage is live it is not possible to pause, rewind or fast forward.
Networks
Bit streaming can be either on demand or .